16. Organizing and Executing Threat Assessments
Organizing and Executing Threat Assessments
ND545 C3 L1 A10 Organizing And Executing Threat Assessments
Overview
Being able to conduct threat assessments enables security professionals to prevent, detect, and respond to attacks. The assessments follow a standard process that includes identifying, analyzing, and prioritizing threats.
Identify
The identification stage includes leverage available information about the business environment and company to start identifying potential threats. The process consists of a combination of brainstorming and using available resources to discover threats both proactively or reactively. Typical activities included in this phase are:
- Threat Detection: The ability to detect threats proactively or reactively in an environment.
- Threat Hunting: Proactively combing through networks to find advanced and undetected threats that may bypass typical security controls and detection technology.
- Threat Actor Discovery: Leverage threat intelligence and other information sources to identify potential threat actors that may impact your business.
Analyze
During the analysis phase, you’ll gather detail and information about the threats you’ve identified and understand how they might apply to your organization. Typical activities included in this phase are:
- Threat Intelligence Gathering: Threat information that has been aggregated, transformed, analyzed, interpreted, or enriched to provide the necessary context for decision-making processes.
- Threat Profiling and Modeling: Analytical insights into trends, technologies, or tactics of an adversarial nature affecting information systems security.
- Threat Scenario Development: A set of discrete threat events, associated with a specific threat source or multiple threat sources, partially ordered in time.
Prioritize
During the final step of prioritization, you consider the variables that matter to the company to determine the most significant threats. Typical activities included in this phase are impact assessment and application of context. As you prioritize the threats based on impact and additional context, you may ask questions like:
- What’s the likelihood that this threat will impact our business?
- How can this threat impact the business?
- What controls are in place to mitigate the impact, if any?
Reference: NIST Computer Resource Center
Introduction to MITRE Cyber Prep Framework
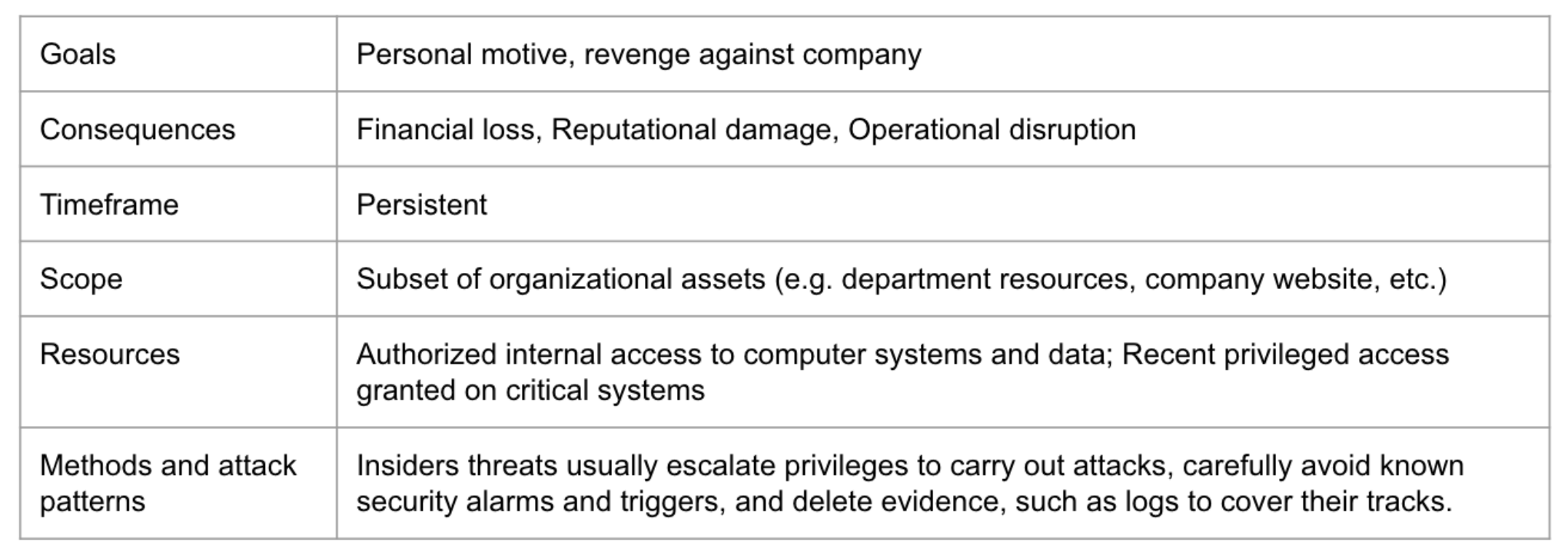
The MITRE Cyber Prep 2.0 framework is a threat-oriented approach that allows an organization to define and articulate its threat assumptions, and to develop organization-appropriate, tailored strategic elements. The framework focuses on advanced threats and corresponding elements of organizational strategy, and also includes coverage of conventional cyber threats. This can serve as a basis for profiling threats. The framework considers threats based on 3 main characteristics: Intent, Target, and Capabilities
Intent
Goal: At what scope or in what arena does the adversary operate? Depending on their goals, an adversary can operate against a subset of the organization’s systems (e.g., its external-facing services); the organization’s operations; the organization’s associates (customers, users, or partners); the organization’s critical infrastructure or industry sector; or the nation. Example goals here are tied back to the threat actors and motivations learned in this lesson.
Consequence: How much of an impact would successful achievement of adversary goals have? How much disruption would adversary activities cause?
Limited or near-term: Will have little or no impact on critical mission operations. Consequences can be handled within an operational planning or funding cycle (e.g., within a business quarter) or within the duration of a mission operation.
Extensive or mid-term: Will have significant impact on critical mission operations, the organization, or its associates. Consequences require remediation or mitigation efforts that extend across operational planning or funding cycles.
Severe or long-term: Will have extremely significant, potentially catastrophic impact on mission operations, the organization, or its associates. Consequences are of a duration or extent that must be considered by strategic planning.
Timeframe: In what timeframe does the adversary operate? Will the adversary’s activities be periodic or episodic, or will the adversary commit to a sustained effort against the organization?
Target
Expanding on the goal of the attack, who or what is the target? The organization might also consider whether it could be an indirect target. Which of our customers or partners could be high-value targets for an adversary?
Capability
What are the likely capabilities and resources of the adversary? Are they minimal, causing the adversary to employ existing, known, malware? Or are they significant, allowing the adversary the benefit of being able to create their own malware, threat vectors, and possibly introduce vulnerabilities into the organization?
ND545 C3 L1 A11 MITRE Framework
Example Threat Profile
ND545 C3 L1 A12 Applying Context To Assess Threats Video V2
Apply Context To Assess and Prioritize Threats
The final step in assessing threat is to consider context that can help you prioritize what’s most critical to the organization. This process varies from company to company, however common elements to consider include:
- The likelihood that the threat will surface.
- The potential impact if the threat is successful at achieving its goal.
- The controls that are in place to mitigate the threat.
The organization also determines a score or rating, such as High, Medium, Low or using a scale of 1-10, in each of the category. For example, a threat that is surely going to cause a loss of life might be scored high in impact. In the same company, a threat that will result in a loss of $1 might be ranked low. This context is then used to rank threats.
In many organizations, this information then feeds the risk management process and it’s important to keep the scoring consistent throughout the process.